Welcome to part 2 of 8 of my series on Kick-Ass WordPress Optimization: Setting Up Your First Server. Here's where we dive into the basics of setting up your very first server that you, regardless of your experience, can set up, manage, and turn into a lean mean blogging machine.
I'm going to assume that you've already done Part 1: Getting Started. If you haven't... for shame! So, get back there and check your list and make sure you're ready to rock!
We'll cover the following topics in this segment:
- Why anyone can do this!
- Virtual Servers – WTF is a Virtual Server and Where Do I Get One?
- Creating Your Virtual Server
- Size and Speed Considerations
- Server Operating Systems – What I recommend.
- Accessing Your Server
- Important Linux Commands
- File Editing – The Basics
- Security Considerations - How to Lock-It-Down
Why Anyone Can Do This
IT and "computer people" have always tried to hold some kind of ridiculous mystery around them. This is a complete shenanigan and, quite frankly, they're no smarter than you regardless of all the jargon they throw out there. Yes it may be geared around computers and technology, but I'm certain an accountant, banker, engineer, or otherwise can talk the same circles around them as they pretend to talk around the rest of us. This said, I've worked in IT for many years, but have also branched out as an engineer, and most recently: engineering sales.
I've met, well, just about every kind of person you can imagine and I've come to find my true talent and craft is being able to explain anything technical to anyone regardless of their education, background, or level of knowledge. I do it every day so I know that YOU are capable! So strap in, grab a beer, and let's do this.
Virtual Servers – WTF is a Virtual Server and Where Do I Get One?
You're probably looking at this line above going... WTF Mike? We're page 2 and you're talking about virtual servers? What the $(*#&! is that? Well, pop that beer you just got and let's dive in. Well, if you want to be fascinated about the world of VR, join the virtual reality workshop!
You've heard about the cloud right? Well, a virtual server exists in the cloud, but for our purposes, you can think of a virtual server as simply a server that someone has conveniently set up for you with a processor, memory (aka RAM), and a hard drive. The great thing about the cloud is that it has a vast number of resources. These resources can be packaged and repackaged as "servers" to allocate specific resources to customers, tasks, etc. This repackaging is what you see as a virtual server.
As discussed earlier, Digital Ocean is my preferred (and this tutorial's baseline) virtual server provider. One of the great reasons I love these guys is they refer to their servers as "Droplets". Cute and catchy, but damned if they don't make my life so much easier. You can create a brand new virtual server (aka "droplet") in 55 seconds with a variety of cpu, memory, and storage options. This is just awesome-sauce and, trust me, a huge time saver! I've been through many a provider and you can't beat the cost and performance here.
So that's a Virtual Server in a nutshell. From here on out, we'll be referring to our virtual server as a "droplet" as I'll be referencing our Digital Ocean host frequently throughout.
Creating Your Virtual Server (or "Droplet")
So we're ready to rock! We're going to essentially build a computer in the cloud! So let's think of this logically like a computer: We'll need a CPU, Memory (RAM), Disk space, an Operating System, a "network card", a location to put it, and potentially a backup system. Keeping this in mind, let's get started.
First we need to log into our Digital Ocean account in order to create our first droplet. This is super simple. So let's get started and get to the login screen.
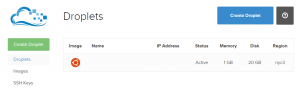
Once you've gotten here and logged in, you should see your dashboard. As you can see here, I've got a single server with 1GB of memory and 20GB of disk space that's based in one of their New York datacenters. You can have as many (or as few) servers as you'd like and this is about as simple as it gets.
Go ahead and click the "Create Droplet" button (big and blue in the top right) and let's get started. You're now on your way to having your very own droplet!
Size and Speed Considerations
The next screen ought to look something like this:
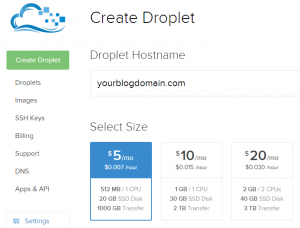
You'll first want to type in your hostname (which is the domain name you own or bought back in the Getting Started section). This is good practice and good form. Additionally, you'll have to do this anyway so make sure you use your website name (ie. "beerlover.com") and then let's take a look at the boxes below that talking about server size.
You'll notice several options here. For your purposes (unless you already have a high-traffic blog you're migrating), you probably don't need anything epic today, so go ahead and pick that $5/mo. server. This will give you a single CPU, 512MB of RAM, and 20GB of disk space. You may think that's not enough to run a server, but fortunately for us, Linux is way leaner than windows and you can optimize the heck out of it. The other great thing about this is that we can always scale up later so if you start to generate lots more traffic, you can simply scale your server up for more CPUs, RAM, and disk space.
Some additional considerations may be if you have a lot of media, you may want to pick a larger size droplet because you need more disk space. If you plan to do lots of computations, you may want to select more CPU and/or RAM. Think about your application and consider the following questions:
- Will you have lots of files and media? Will you allow uploads by users? If so, more disk space will be wise.
- Will you have lots of computations or do you already have a high-traffic site? If so, consider more CPUs and/or Memory (RAM).
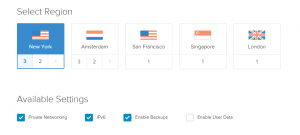
You'll want to scroll down and select your droplet location next. I'd recommend selecting a location that's closest to you or your intended user-base. Personally, the New York and Amsterdam locations are preferential as they have features like Private Networking (which you very likely will want if you intend to scale up later) which we will discuss later.
For our purposes, go ahead and check Private Networking, IPV6, and Enable Backups. Note, enabling backups costs 20% of your monthly server cost, so if you selected $5, it would be $1, $10 then $2, and so on. Being that we never know what may happen in the world of datacenters, and depending on how important you feel your work is, you'll probably want to check this.
That should get us started down the right path, so let's scroll down again and move on to the next steps and get to selecting your operating system.
Server Operating Systems
Now, if you're like most folks, you have a Mac or PC at home.... really these are the only two options for personal computing these days. Whatever your case, you're all running some version of an Operating System whether it be Windows, Mac OSX, and in the less usual case, Linux.
Your server is no different! You'll need an operating system to run your server and the applications (web server, database, etc) to serve up piping hot WordPress awesome-sauce. You'll note that Windows is not an option here. This is a good thing as Linux is the right choice for high-reliability / high-performance web servers.
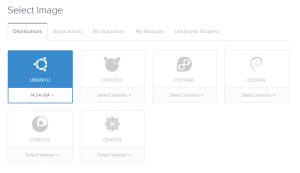
What you'll see here is names like Ubuntu, FreeBSD, Fedora, etc. You see, Linux is a lot like lollipops, it's got a bunch of different flavors, but at the core, they're all made of sugar. Linux has different flavors of Distributions that contain differences, but at the core, they're all still Linux. Knowing this, my favorite, and really easy to work with is: Ubuntu.
For our purposes, let's select Ubuntu 14.04 x64 as our distribution for our droplet. This means we will have the 64-bit Ubuntu Linux version 14.04 operating system running on our server. This is important as the .04 is what is considered "Long Term support" by the makers of Ubuntu and will have system updates, patches, and important security items for a long time from now.
Skip over the other tabs (Applications, My Snapshots, etc) as you will not be needing any of this and any other options selected will confuse the situation.
Accessing Your Server
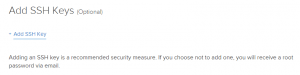
The final piece here asks for an SSH Key (Optional). If you are familiar with this method of access, go ahead and add your key. If you are unfamiliar with this, it's not really necessary, so please skip this option and read on!
At this point, whether or not you added your SSH key, you can go ahead and create your droplet. If you did not add a key, a password will be sent to your e-mail. You'll want this! Go ahead and click the "Create Droplet" button now and sit back for the next 55 seconds!
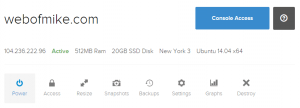
You'll see your droplet dashboard when creation is complete:
At this point, check your e-mail. You should have received an e-mail containing some important information regarding your server. I'd go ahead and print this or have it nearby as you'll need it during this process. See below for the list of information you'll need that will be contained in this e-mail:
Droplet Name: webofmike.com IPv4 Address: XXX.XXX.XXX.XXX IPv6 Address: 2604:A880:0800:0010:0000:0000:XXXX:XXXX/64 Username: root Password: XXXXXXXXX
You'll note I've marked out sensitive information with X's. Make sure you either shred or burn or swallow this paper if you have printed it. But really, you want to keep this information safe! It's essentially the keys to your server so don't share this.
Now, you'll need a way to access your server! The majority use the SSH or "Secure Shell" method. This provides an end-to-end encrypted solution to accessing your server to keep out the nasties and the bad people. This is industry standard, so you'll be using it. Fortunately for us, there's very little differences in if you're using Mac OSX or Windows, but I'll cover these right here and we shouldn't have to revisit these differences later.
For Mac OSX users (Windows users you can skip this):
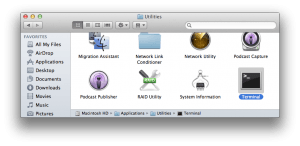
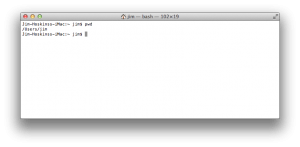
You'll be using the Terminal program. On OS X, open your Applications folder, then open the Utilities folder. Open the Terminal application. You may want to add this to your dock. I like to launch terminal by using Spotlight search in OS X, searching for “terminal”.
Once you open this, you should see a page that looks like this:
Each prompt allows you to type a command you can then execute (anyone here remember DOS? Kinda like that but it doesn't suck) to run programs and system commands.
For you Mac users, go ahead and get that IPV4 address that was sent in your Digital Ocean droplet e-mail. Should look like this: 103.236.85.188 (or something like that). You're going to then type into your command line the following:
Your-Computer:~ mike: ssh [email protected]
You will then be prompted by a message that looks a little something like this:
The authenticity of host 'blah.blah.blah (10.10.10.10)' can't be established. RSA key fingerprint is a4:d9:a4:d9:a4:d9a4:d9:a4:d9a4:d9a4:d9a4:d9a4:d9a4:d9. Are you sure you want to continue connecting (yes/no)?
Just type 'yes' here. Essentially your computer has never seen your server before and this is making sure that secure communications are maintained. Then skip over this next part for Windows as it'll all be the same from here on out.
Windows Users (Mac users you can skip this):
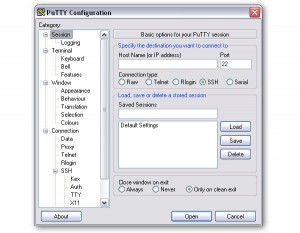
For Windows, we have to go a slightly different route. We're going to use an access program called PuTTY. You can download it here. Once you have downloaded the program, it's a single executable file so place it on your Desktop (or wherever you want to keep this) and open the program.
You should have a screen that looks like this:
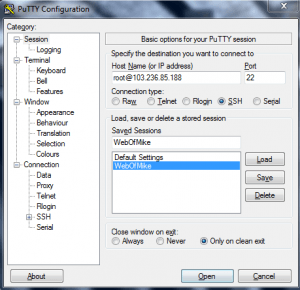
In the box that says "Host Name (or IP address)" type the following (and replace the IPV4 address with the one from your droplet creation e-mail.
root@
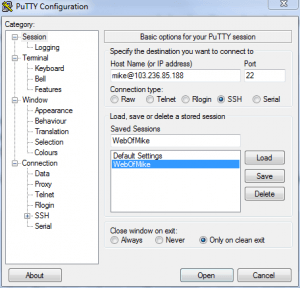
In the "Saved Sessions" text box, type the name of your server (for instance, "webofmike.com") and click Save. You should have a screen that looks like this now:
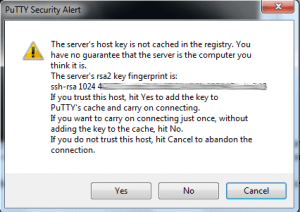
You can now double-click the name in the Saved Sessions list and PuTTY will attempt to login. You may see a message that looks like this:
Just go ahead and click Yes here. Essentially your computer has never seen your server before and this is making sure that secure communications are maintained.
Continuing on (we're done with Mac/Windows differences):
When asked for your password, simply type in the one that Digital Ocean generated for you. If you have lost this, log back into your Digital Ocean panel and reset the root password for your droplet. Hint: You can do this from your droplet dashboard under the Access tab.
Once you've logged in, you'll see a screen with text that looks like the following:
Using username "root".
Authenticating with public key "dsa-key-20121126"
Welcome to Ubuntu 14.04.1 LTS (GNU/Linux 3.13.0-37-generic x86_64)
* Documentation: https://help.ubuntu.com/
System information as of Sun Feb 1 10:00:50 EST 2015
System load: 0.3 Processes: 84
Usage of /: 22.6% of 19.56GB Users logged in: 0
Memory usage: 28% IP address for eth0: 103.236.85.188
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
93 packages can be updated.
46 updates are security updates.
Last login: Sun Feb 1 10:00:51 2015 from 162-233-236-135.lightspeed.chrlnc.sbcglobal.net
root@webofmike:~#
This is YOUR server command line! Congratulations, you now are the administrator of your very first server! Now, we're going to move on to some basics and important steps to navigate, administrate, and secure your server like a boss.
Important Linux Commands
So, now that we're into our system, I bet you're asking yourself: "Now what?". Now we need to know a few basic commands:
pwd: Present Working Directory
This command shows us what directory you are currently in in your filesystem. Think of your server as a file structure with the top level being "/". This is the base directory for all of your files. The command pwd will show you what directory you're working in should you get lost.
root@webofmike:~# pwd /root
cd: Change Directory
The cd command allows you to traverse your filesystem. For example, the following command will take you to the /home/ directory:
root@webofmike:~# cd /home/ root@webofmike:/home#
ls: List directory contents
The ls command will allow you to see all of the directory contents (files, folders, etc) in the directory you're in.
root@webofmike:/home# ls mike
passwd: Change your users password.
This is rather important and we'll certainly cover this in the security section. This allows you to change your password to log in to your server.
root@webofmike:~# passwd Enter new UNIX password: Retype new UNIX password: passwd: password changed
reboot: Reboot your server.
You'll need to be the root (administrator) user or have root (administrative) privileges. We'll show you how to get this done in Security Considerations below.
I certainly will be covering more as we go through this tutorial and will attempt to make sure to explain any new ones that we may come across.
File Editing – The Basics
Now, for a very long time and about as far back as I can remember people using Linux, the command-line file-editor of choice has often been vi or vim. While this is considered a great tool... I generally like to use nano instead. Nano is a great tool and this is what we'll be using because it's easier and equally good for our purposes.
Starting nano from the command line:
To edit a file called "filename", type:
mike@webofmike:~$ nano filename
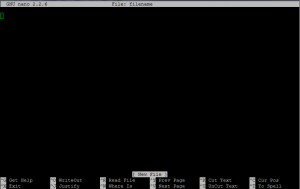
You should then see a screen that looks a lot like this:
The usual mouse-based point-and-click method is not supported by nano. You must use the arrow keys to move around the page in nano.
Common nano navigation commands include:
Ctrl + A: move to beginning of line.
Ctrl + E: move to end of line.
Ctrl + Y: move down a page.
Ctrl + V: move up a page.
Ctrl + _: move to a specific line (^^V moves to the top of the file, ^^Y to the bottom).
Ctrl + C: find out what line the cursor is currently on.
Ctrl + W: search for some text.
Ctrl + K: Cut current line.
Ctrl + O: Output (save) the current file.
Ctrl + X: Exit nano.
We will be using this editor for now, so feel free to get comfortable with it before you move on.
Security Considerations and How to Lock-It-Down
One of the single most important things you will do happens right here. Securing your server from people that mean to do your server harm, and most importantly: you! That's right, making sure you don't accidentally mess things up is super important. That said, let's get into it.
Creating your user:
At this point, we've been using a root (administrator) account. This is never recommended and really needs to be changed so you have your own user. In order to create your user (we'll use my name as an example) type the following:
root@webofmike:~$ useradd -g sudo -m -b /home/ mike
This should do a few things:
- "useradd ... mike": Creates your user in the system.
- "-m -b /home/": Creates a directory for your user in the /home/ directory.
- "-g sudo": Adds your user to the "sudo" group. This is important for later.
Now we need to set your password in order to let you login with this user. Type the "passwd
root@webofmike:~# passwd mike Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully
Once this is done, type "exit". This will disconnect you from the system and now you'll reconnect as your user as we move forward. Once you've disconnected, go back to the step where we setup our SSH connection and change the "root" use to your user:
or for you Mac users, your Terminal command should look like this:
ssh [email protected]
Now reconnect to your server. Use the new password you just set and you'll notice you're logged in as your user!
Now, as we move forward, we're going to use a command in front of most of our commands in order to give our new user administrative privileges on a per-command basis. This command is called: sudo. The beauty of sudo is that you can grant root access to certain users without giving them the root password. On top of that, you can specify only to grant them access to certain commands on certain hosts. Best of all, sudo logs every command that is run through it, so you can easily track down any issues that may arise.
So, now that we're back in, you'll see something looking a bit like this:
mike@webofmike:~#
You'll notice you're user is the first text in the prompt indicating that your new user is the one you're working with.
The Firewall
You're all probably very familiar with the concept of a firewall, but just in case you are not: A firewall is a software program or piece of hardware that helps screen network traffic and keep out hackers, viruses, and worms that try to reach your server over the Internet. That's about the nuts and bolts of what we're about to configure.
As we're currently logged in as our regular user, we'll need to elevate our privileges to do the administrative task of configuring your new firewall. For this, we're going to use a common Linux firewall: iptables. So let's get started configuring your firewall.
Unless you have done anything with this before, it's highly unlikely that there are any rules in your firewall at this point in time. Even if that's the case, we're going to flush out all of the iptables rules and start with a clean slate. So, let's go to our server's and type:
mike@webofmike:~# sudo iptables -P INPUT ACCEPT mike@webofmike:~# sudo iptables -P OUTPUT ACCEPT mike@webofmike:~# sudo iptables -F
This will flush any and all rules out and now we have a blank slate to design our rules to let traffic in and out of our server. So now we can go ahead an put in our first rule. This rule is exceedingly important as it will describe our current SSH connection. This will allow us to watch connections as they come in and keep track of them to ensure nothing malicious is going on:
mike@webofmike:~# sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT mike@webofmike:~# sudo iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
This is now your first rule in your firewall! You're on your way to a better safer server. Next we're going to put in rules allowing two things: your SSH access and your web server that you will be setting up. These services run on ports 22 and 80 respectively and we will be allowing yourself, and other users to connect on these ports in order to access your web site. To allow ports 22 (SSH) and 80 (web server) type the following:
mike@webofmike:~# sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT mike@webofmike:~# sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
Now we explicitly allow these two connections to our server and we can move onto the next step of our process by denying any other access. We can do this by explicitly telling our server to drop any connections or packets that we have not already authorized. We're going to ensure our first policy is to accept all connections, then process our rules, and then drop anything that is left. Do this by typing the following:
mike@webofmike:~# sudo iptables -P INPUT ACCEPT mike@webofmike:~# sudo iptables -A INPUT -j DROP
Now that we've completed these steps, we're going to make sure we save these rules so anytime we may need to reboot (this will be very rare) these rules will always apply and you should not have to do this again. To do this, we're going to update our list of possible programs we can install by typing:
mike@webofmike:~# sudo apt-get update
This will be followed by a large amount of text... This is just your system updating, so wait it out. Once this is done, we'll install iptables-persistence using the following command:
mike@webofmike:~# sudo apt-get install iptables-persistent
Answer yes to the following two questions and you're all set. These are the very basics. I will post more on this topic in a later series or posts on further security measures, but for now, this will do quite well.
Now that we're done here and you have a fully functioning and secured server, let's move on to our next step in WordPress Optimization: Setting Up a Web Server ».